
Ransomware attacks are on the rise, up by 13% in the past five years, causing companies an average downtime of 24 days, with an average cost of roughly $1.85 million per incident.
As ransomware threats continue to evolve, businesses must embrace a dynamic and layered approach to protect their Windows devices.
Microsoft Intune and Windows’ built-in ransomware protection mechanisms offer unparalleled advantages for organizations aiming to safeguard their digital assets. Expanding on the essential strategies previously discussed, let’s dive deeper into how these tools work together to provide comprehensive security.
Windows devices, particularly those running Windows 11, come with a suite of native security tools designed to combat malware and ransomware. The cornerstone of this protection is Windows Defender, a robust next generation antivirus and threat detection program integrated into the operating system.
Windows Defender ransomware protection includes several key features, such as real-time threat detection, malware scanning, and the ability to block suspicious activities before they escalate. One of the standout features is Controlled Folder Access, which specifically targets ransomware. By restricting unauthorized access to designated folders, this feature ensures that critical files remain safe even if other parts of the system are compromised.
Maintaining consistent configurations across multiple devices in an organization can be challenging without centralized control. This is where Microsoft Intune becomes invaluable, enabling IT administrators to enforce these settings uniformly across all endpoints.
Windows 11 builds on the security foundation of Windows 10 with new features designed to address emerging threats, including ransomware. Hardware-based security enhancements, such as the Trusted Platform Module and virtualization-based security (VBS), make it even more challenging for attackers to compromise devices.
Managing ransomware protection in Windows 11 with Intune ensures that businesses can take full advantage of these advanced features. For example, administrators can configure policies to enforce VBS, ensuring that all devices benefit from this additional layer of protection.
Microsoft’s security ecosystem also includes access to a vast network of threat intelligence, providing insights into emerging ransomware trends. Intune integrates with these resources, giving administrators the information they need to adjust their security policies and respond to new threats.
One of the most significant challenges in ransomware prevention is ensuring that all devices in an organization adhere to the same security policies. Intune addresses this by enabling administrators to deploy policies that enforce features like Controlled Folder Access and periodic scans. By automating these processes, Intune removes the risk of human error or negligence that can leave devices vulnerable.
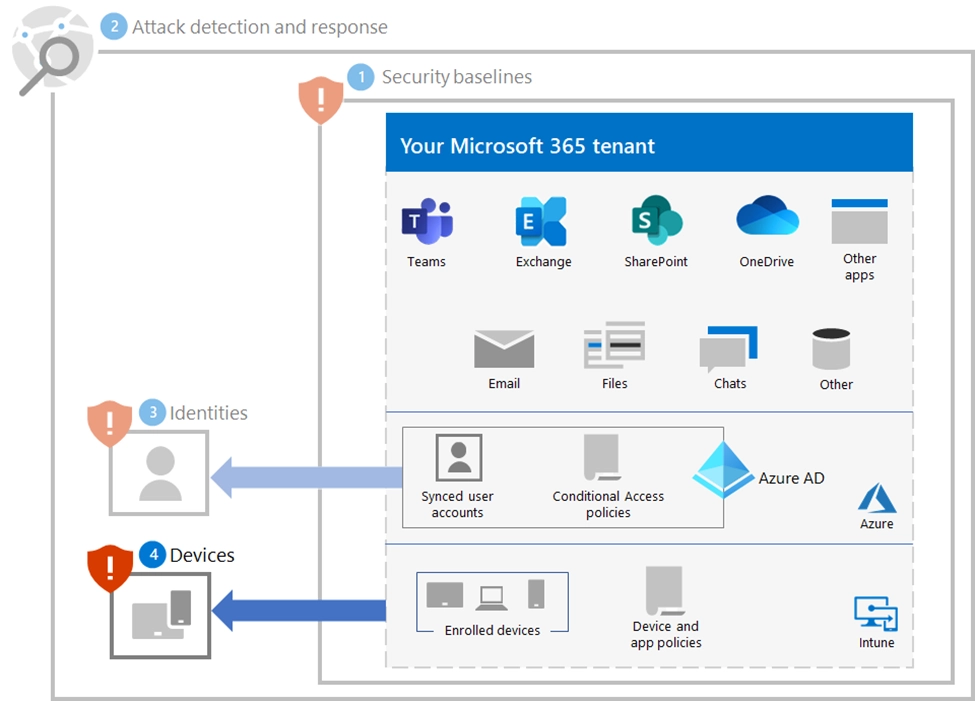
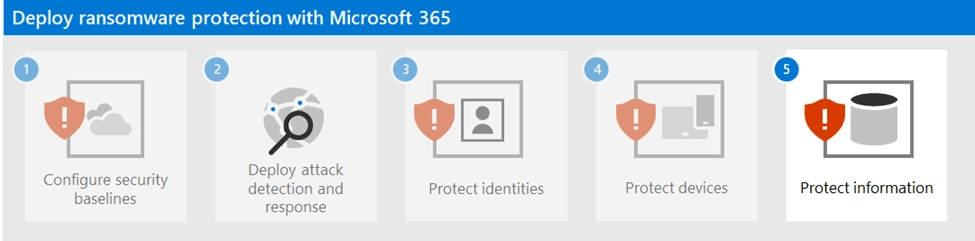
For example, administrators can configure Intune to ensure that Windows Defender ransomware protection remains active on all devices. This includes setting real-time protection, enabling cloud-delivered protection, and enforcing Controlled Folder Access. These settings can be locked to prevent users from disabling them, maintaining a consistent security baseline.
Ransomware often infiltrates systems through seemingly benign activities, such as phishing emails or compromised websites. Detecting these threats early requires constant vigilance and the ability to analyze vast amounts of data for unusual patterns. Intune’s integration with Microsoft Defender for Endpoint offers advanced analytics capabilities, allowing organizations to monitor device activity and detect potential threats in real-time.
This proactive approach means that administrators can identify and mitigate ransomware attacks before they cause significant damage. By using Intune’s alerting system, businesses can respond quickly to suspicious activities, isolating affected devices and preventing the spread of ransomware across the network.
Implementing role-based access control (RBAC) is a critical component of ransomware prevention. By restricting access to sensitive files and systems based on job roles, businesses can minimize the impact of a ransomware attack. Intune makes it easy to configure RBAC policies, ensuring that employees only have access to the resources they need.
This principle of least privilege is particularly important for preventing ransomware from spreading through an organization. Even if one device is compromised, limiting access ensures that the attack cannot reach critical systems or sensitive data.
No matter how robust your ransomware prevention strategy is, the possibility of an attack cannot be entirely eliminated. This makes data backup an essential component of any comprehensive security plan. Regular backups ensure that businesses can restore their systems and data without paying a ransom, minimizing downtime and financial losses.
Microsoft Intune simplifies the implementation of cloud-based backup solutions by automating backup schedules and ensuring that critical data is stored securely. Integration with Microsoft OneDrive and Azure Backup allows businesses to maintain multiple copies of their data, providing an additional layer of protection against ransomware.
Endpoint hardening is a critical aspect of ransomware prevention. By securing individual devices, organizations can limit the spread and impact of a ransomware attack. Intune offers several tools to enhance endpoint security, including application whitelisting, device encryption, and firewall management.
Through application control policies, businesses can specify which programs are allowed to run on their systems, preventing malicious applications from executing. Intune also facilitates BitLocker encryption for Windows devices, ensuring that sensitive data remains inaccessible even if a device falls into the wrong hands.
Ransomware attacks often involve stealthy tactics, such as fileless malware or exploiting zero-day vulnerabilities. Detecting these sophisticated threats requires advanced tools capable of analyzing behaviors and identifying anomalies. Intune’s integration with Microsoft Defender for Endpoint offers unparalleled threat detection and response capabilities.
Defender for Endpoint uses machine learning and artificial intelligence to detect potential ransomware threats in real time. For example, if unusual file encryption activity is detected, Defender for Endpoint can automatically isolate the affected device, stopping the ransomware from spreading further. These automated responses are critical for minimizing the damage caused by ransomware attacks.
Despite the best defenses, organizations must prepare for the possibility of a successful ransomware attack. A robust recovery plan is essential for minimizing downtime and ensuring business continuity. Microsoft Intune plays a key role in facilitating recovery by automating data restoration and device re-provisioning.
Using Intune, administrators can deploy configurations that ensure critical files are regularly backed up to Microsoft OneDrive or Azure Cloud. These backups provide an essential safety net, allowing organizations to restore encrypted data without succumbing to ransom demands. Intune also simplifies the process of re-imaging infected devices, enabling businesses to resume operations quickly.
The ransomware threat landscape continues to evolve, driven by increasingly sophisticated attackers and emerging technologies. To stay protected, businesses must adopt adaptive security strategies using advanced tools. With guidance from Microsoft Intune consultants, your organization can leverage Intune and Windows’ built-in protections for cutting-edge ransomware defense, ensuring you stay one step ahead of cyber threats.
By combining proactive policy enforcement, advanced threat detection, and user education, businesses can create a robust security posture that minimizes the risk of ransomware. With Microsoft Intune at the center of this strategy, organizations can confidently navigate the challenges of an ever-changing digital environment while ensuring the safety of their critical assets. CloudSolvers can help you implement a comprehensive solution to protect your organization from Ransomware. Let’s work together to secure your future. Join us in building a secure future together.