
As of 2024, 57% of organizations report experiencing phishing attempts weekly or even daily. With phishing accounting for 80% of IT security incidents, it’s estimated that businesses lose approximately $17,700 every minute due to phishing-related issues.
This makes phishing one of the largest threats to your organization. Thankfully, Microsoft Intune has you covered and can offer peace of mind to leaders focused on data protection.
Microsoft Intune integrates with Defender for Enpoints and enables administrators to manage conditional access policies to help mitigate phishing attempts and the damage they can do to your organization.
Conditional Access, part of Microsoft Entra ID (formerly Azure Active Directory), enables organizations to create policies that combine user, device, and application signals to determine access permissions.
Intune integrates with Conditional Access to enhance security by enforcing device compliance and app protection policies. This ensures a secure, flexible experience for users to access corporate resources from various devices and locations.
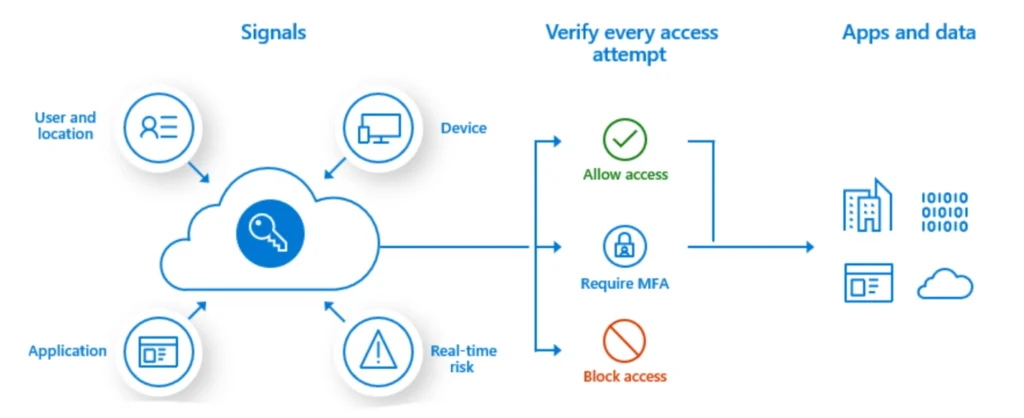
The first line of defense is device-based conditional access. Intune and Entra ID ensure that only devices managed through Intune can access organizational resources like email, SaaS applications, and other important applications and information.
You can also make it so that only domain-joined devices enrolled in Intune can have access to Microsoft 365 services based on network access, device risk, or whether or not they are on-premises.
Microsoft Intune enforces policies using various signals to ensure security and compliance. It can restrict access based on organizational roles, enforce standards like operating system versions and security configurations, ensure that only managed applications access sensitive data, adjust restrictions based on location, and leverage real-time risk assessments through integration with Microsoft Defender.
Keep in mind that the complaint network location features are only supported by devices enrolled in mobile device management (MDM). Users who aren’t enrolled in MDM may be blocked from accessing key resources.
Microsoft Defender SmartScreen's Enhanced Phishing Protection is an advanced security feature that safeguards users from phishing attacks by providing proactive warnings and mitigation strategies. This feature integrates seamlessly into the operating system, offering an extra layer of defense for sensitive information like passwords, preventing their exposure to unsafe applications, websites, and processes.
Features such as these integrate with Microsoft Intune allowing IT administrators to configure and enforce policies related to phishing protection.
This integration provides organizations with a centralized mechanism to protect user credentials across all managed devices, ensuring compliance with security standards. Administrators can enable or customize phishing protection features, such as warning users against password reuse or preventing unsafe password storage and blocking malicious websites, to align with organizational security policies.
Enhanced Phishing Protection works dynamically, leveraging Microsoft's intelligent threat detection systems to identify potential risks when users enter passwords into websites or applications.
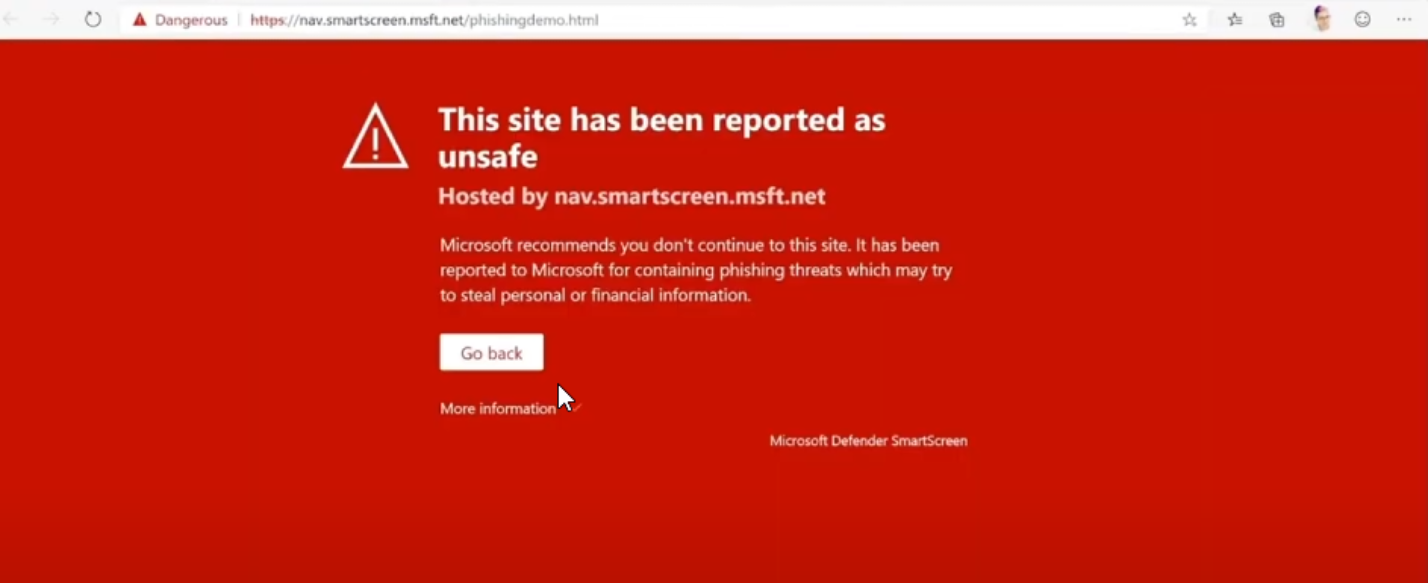
For instance, if a user enters their Microsoft account password into a known malicious or unfamiliar website, SmartScreen triggers a warning.
This alert is a result of extensive analysis, which includes evaluating the site's reputation and the context of the password entry. The warning prompts users to reconsider their actions, offering advice on best practices for safeguarding credentials.
This feature is also designed to prevent the reuse of corporate passwords across personal applications or sites. Password reuse is critical because it increases the risk of credential stuffing attacks, where cybercriminals exploit reused passwords across multiple sites to gain unauthorized access.
By discouraging and alerting users to this behavior, Enhanced Phishing Protection helps mitigate such vulnerabilities and reinforces better password hygiene.
Another significant aspect of Enhanced Phishing Protection is its ability to detect unsafe storage of passwords. Users sometimes store passwords in plain text files or unencrypted documents on their devices, which malicious actors can easily access.
SmartScreen scans these files and alerts users when such unsafe storage practices are detected, encouraging them to adopt more secure methods of storing credentials.
SmartScreen's capabilities are further enhanced through its connection with the broader Microsoft security ecosystem. It leverages threat intelligence from Microsoft Defender, enabling it to stay updated with the latest phishing trends and malicious domains.
This real-time intelligence helps ensure that SmartScreen can quickly identify and block emerging threats, providing users with up-to-date protection and supporting a user-centric approach to security by offering clear and actionable guidance when alerts are triggered. Instead of overwhelming users with technical jargon, SmartScreen presents straightforward instructions on how to mitigate the detected threat.
For example, if a user is warned about password reuse, the system provides recommendations for creating strong, unique passwords or using a trusted password manager.
In enterprise environments, Enhanced Phishing Protection offers additional benefits by integrating with security monitoring and reporting tools. IT teams can view insights into phishing attempts and user behavior, enabling them to identify trends and potential vulnerabilities. These insights support proactive security measures, helping organizations stay ahead of evolving threats.
Attack Surface Reduction (ASR) rules, an integral feature of Microsoft Defender with Intune, are critical in safeguarding organizational networks against various cybersecurity threats. Designed to minimize the exploitable vulnerabilities in an enterprise's IT infrastructure, ASR rules target the techniques commonly used by malicious actors. These techniques often exploit gaps in application behavior, scripting engines, and user activities to gain unauthorized access or deploy harmful payloads.
By enforcing strict control over specific types of activities, ASR rules reduce the risk of breaches, enhancing the organization's overall security posture.
ASR rules are proactive security measures that prevent threats before they execute. Rather than relying solely on post-execution detection mechanisms, these rules block potentially harmful actions at the source. This approach is vital for combating advanced persistent threats (APTs) and zero-day exploits, where traditional antivirus solutions may lag in detection. For example, ASR rules can prevent untrusted applications from launching child processes, blocking a common tactic used in lateral movement within networks or in malware propagation.
The implementation of ASR rules provides organizations with a granular level of control over device activities. Administrators can configure rules to suit their unique security requirements, striking a balance between stringent protection and operational flexibility.
Each rule targets specific behaviors, such as executing scripts from email attachments, embedding macros in Office files, or attempting code injection. These rules are often based on the analysis of attack patterns observed in the wild, ensuring that they address real-world threats.
Integration with Microsoft Defender allows ASR rules to leverage insights from the broader Microsoft security ecosystem. This integration ensures that rules are continuously updated to reflect the latest threat intelligence, enabling real-time defense against evolving cyberattacks.
The system also provides detailed reporting and alerting features, giving administrators visibility into rule enforcement and blocked activities. This data can be used to refine security policies, ensuring they remain effective without causing unnecessary disruptions.
A key feature of ASR rules is their ability to operate in audit mode. This mode allows administrators to test the impact of specific rules before fully enforcing them. By logging the activities that would have been blocked, organizations can evaluate the potential operational impact and adjust rules accordingly. This approach minimizes the risk of false positives, ensuring that legitimate business processes are not hindered by overly restrictive policies.
ASR rules address the human element of cybersecurity, recognizing that user actions are a significant vector for threats. By blocking actions like running executable content from email attachments and other phishing attempts, ASR rules help mitigate risks associated with user errors or deliberate misuse. These measures are particularly important in mitigating phishing attacks, which often rely on tricking users into executing malicious files or links.
In addition to targeting application behaviors, ASR rules can be configured to protect against credential theft. For instance, rules can prevent processes from accessing local security authority subsystem service (LSASS) memory, a technique often used in credential dumping attacks. This capability is critical in environments where sensitive credentials, such as administrator passwords, are prime targets for attackers.
ASR rules are not a standalone solution but a critical component of a layered security strategy. They complement other Microsoft Defender features, such as endpoint detection and response (EDR), vulnerability management, and network protection. Together, these tools create a comprehensive defense-in-depth approach capable of addressing threats across all stages of the attack lifecycle.
For organizations operating in highly regulated industries, ASR rules also offer compliance benefits. By demonstrating proactive measures to secure endpoints and reduce attack surfaces, businesses can meet regulatory requirements and improve their security audits. This added layer of accountability reinforces trust with stakeholders and aligns security efforts with broader organizational goals.
Microsoft’s Attack Simulation Training offers organizations an effective way to assess and enhance their security preparedness against phishing attacks. The tool enables administrators to create and run realistic simulations of common social engineering techniques, such as credential harvesting, malware attachments, and drive-by URLs. By testing user susceptibility to these simulated threats, organizations can identify vulnerabilities and address them before they are exploited in real-world scenarios.
Setting up a simulation involves using the Microsoft Defender portal to configure attack parameters, including the type of threat, payload delivery method, and target recipients. Administrators can schedule simulations and monitor their progress in real-time. Once a campaign is complete, the tool provides detailed analytics, showing how users interacted with the simulated phishing emails. You can then use these insights to highlight areas for improvement and guide the development of tailored security awareness training.
Integration of attack simulation training into the broader Microsoft security ecosystem ensures a seamless and comprehensive approach to organizational defense. By combining technical safeguards with user education, you can foster a security-first culture, strengthen an organization’s ability to mitigate risks, stay ahead of evolving threats, and maintain a resilient cybersecurity posture.
The ability to customize Intune’s various tool rules is one of its strengths, but it also underscores the importance of continuous monitoring and refinement. Cyber threats are dynamic, and security measures must adapt to remain effective.
Administrators should regularly review rule and policy performance, analyze blocked activities, and update configurations based on the latest threat intelligence. This iterative process ensures your policies remain relevant and effective against emerging threats. Although not an Intune feature, the Microsoft Defender simulation training platform is an innovative solution designed to bolster an organization’s cybersecurity defenses, providing a centralized hub for simulating phishing and other cyberattack scenarios. This tool enables businesses to simulate real-world cyberattacks, train employees to recognize and mitigate threats, and ultimately improve overall security posture.
The platform equips companies with the knowledge and tools necessary to stay ahead of potential threats. Unlike traditional methods, which often rely on static modules, this platform offers dynamic and engaging training sessions that are automatically customized based on an employee’s performance in simulated attacks. For instance, if an employee falls for a simulated phishing email, the platform assigns targeted training to address that specific vulnerability. This adaptive learning process ensures that employees are continuously improving their awareness and response capabilities.
Phishing attacks remain one of the most significant cybersecurity threats organizations face, causing widespread damage and financial loss. With Microsoft Intune’s robust integration with tools like Defender SmartScreen, Conditional Access, and Attack Surface Reduction rules, your organization can stay ahead of phishing attempts and other cyber threats. Intune empowers administrators to enforce tailored security policies, safeguard sensitive data, and create a secure environment for users—no matter where they work.
Ready to fortify your organization’s defenses against phishing attacks? Contact CloudSolvers today to learn how our expert Intune services can help you implement and optimize Microsoft Intune for comprehensive protection. Let’s work together to secure your future.

Ransomware attacks are on the rise, up by 13% in the past five years, causing companies an average downtime of 24 days, with an average cost of roughly $1.85 million per incident.
As ransomware threats continue to evolve, businesses must embrace a dynamic and layered approach to protect their Windows devices.
Microsoft Intune and Windows' built-in ransomware protection mechanisms offer unparalleled advantages for organizations aiming to safeguard their digital assets. Expanding on the essential strategies previously discussed, let’s dive deeper into how these tools work together to provide comprehensive security.
Windows devices, particularly those running Windows 11, come with a suite of native security tools designed to combat malware and ransomware. The cornerstone of this protection is Windows Defender, a robust next generation antivirus and threat detection program integrated into the operating system.
Windows Defender ransomware protection includes several key features, such as real-time threat detection, malware scanning, and the ability to block suspicious activities before they escalate. One of the standout features is Controlled Folder Access, which specifically targets ransomware. By restricting unauthorized access to designated folders, this feature ensures that critical files remain safe even if other parts of the system are compromised.
Maintaining consistent configurations across multiple devices in an organization can be challenging without centralized control. This is where Microsoft Intune becomes invaluable, enabling IT administrators to enforce these settings uniformly across all endpoints.
Windows 11 builds on the security foundation of Windows 10 with new features designed to address emerging threats, including ransomware. Hardware-based security enhancements, such as the Trusted Platform Module and virtualization-based security (VBS), make it even more challenging for attackers to compromise devices.
Managing ransomware protection in Windows 11 with Intune ensures that businesses can take full advantage of these advanced features. For example, administrators can configure policies to enforce VBS, ensuring that all devices benefit from this additional layer of protection.
Microsoft's security ecosystem also includes access to a vast network of threat intelligence, providing insights into emerging ransomware trends. Intune integrates with these resources, giving administrators the information they need to adjust their security policies and respond to new threats.
One of the most significant challenges in ransomware prevention is ensuring that all devices in an organization adhere to the same security policies. Intune addresses this by enabling administrators to deploy policies that enforce features like Controlled Folder Access and periodic scans. By automating these processes, Intune removes the risk of human error or negligence that can leave devices vulnerable.
For example, administrators can configure Intune to ensure that Windows Defender ransomware protection remains active on all devices. This includes setting real-time protection, enabling cloud-delivered protection, and enforcing Controlled Folder Access. These settings can be locked to prevent users from disabling them, maintaining a consistent security baseline.
Ransomware often infiltrates systems through seemingly benign activities, such as phishing emails or compromised websites. Detecting these threats early requires constant vigilance and the ability to analyze vast amounts of data for unusual patterns. Intune’s integration with Microsoft Defender for Endpoint offers advanced analytics capabilities, allowing organizations to monitor device activity and detect potential threats in real-time.
This proactive approach means that administrators can identify and mitigate ransomware attacks before they cause significant damage. By using Intune's alerting system, businesses can respond quickly to suspicious activities, isolating affected devices and preventing the spread of ransomware across the network.
Implementing role-based access control (RBAC) is a critical component of ransomware prevention. By restricting access to sensitive files and systems based on job roles, businesses can minimize the impact of a ransomware attack. Intune makes it easy to configure RBAC policies, ensuring that employees only have access to the resources they need.
This principle of least privilege is particularly important for preventing ransomware from spreading through an organization. Even if one device is compromised, limiting access ensures that the attack cannot reach critical systems or sensitive data.
No matter how robust your ransomware prevention strategy is, the possibility of an attack cannot be entirely eliminated. This makes data backup an essential component of any comprehensive security plan. Regular backups ensure that businesses can restore their systems and data without paying a ransom, minimizing downtime and financial losses.
Microsoft Intune simplifies the implementation of cloud-based backup solutions by automating backup schedules and ensuring that critical data is stored securely. Integration with Microsoft OneDrive and Azure Backup allows businesses to maintain multiple copies of their data, providing an additional layer of protection against ransomware.
Endpoint hardening is a critical aspect of ransomware prevention. By securing individual devices, organizations can limit the spread and impact of a ransomware attack. Intune offers several tools to enhance endpoint security, including application whitelisting, device encryption, and firewall management.
Through application control policies, businesses can specify which programs are allowed to run on their systems, preventing malicious applications from executing. Intune also facilitates BitLocker encryption for Windows devices, ensuring that sensitive data remains inaccessible even if a device falls into the wrong hands.
Ransomware attacks often involve stealthy tactics, such as fileless malware or exploiting zero-day vulnerabilities. Detecting these sophisticated threats requires advanced tools capable of analyzing behaviors and identifying anomalies. Intune’s integration with Microsoft Defender for Endpoint offers unparalleled threat detection and response capabilities.
Defender for Endpoint uses machine learning and artificial intelligence to detect potential ransomware threats in real time. For example, if unusual file encryption activity is detected, Defender for Endpoint can automatically isolate the affected device, stopping the ransomware from spreading further. These automated responses are critical for minimizing the damage caused by ransomware attacks.
Despite the best defenses, organizations must prepare for the possibility of a successful ransomware attack. A robust recovery plan is essential for minimizing downtime and ensuring business continuity. Microsoft Intune plays a key role in facilitating recovery by automating data restoration and device re-provisioning.
Using Intune, administrators can deploy configurations that ensure critical files are regularly backed up to Microsoft OneDrive or Azure Cloud. These backups provide an essential safety net, allowing organizations to restore encrypted data without succumbing to ransom demands. Intune also simplifies the process of re-imaging infected devices, enabling businesses to resume operations quickly.
The ransomware threat landscape continues to evolve, driven by increasingly sophisticated attackers and emerging technologies. To stay protected, businesses must adopt adaptive security strategies using advanced tools. With guidance from Microsoft Intune consultants, your organization can leverage Intune and Windows’ built-in protections for cutting-edge ransomware defense, ensuring you stay one step ahead of cyber threats.
By combining proactive policy enforcement, advanced threat detection, and user education, businesses can create a robust security posture that minimizes the risk of ransomware. With Microsoft Intune at the center of this strategy, organizations can confidently navigate the challenges of an ever-changing digital environment while ensuring the safety of their critical assets. CloudSolvers can help you implement a comprehensive solution to protect your organization from Ransomware. Let’s work together to secure your future. Join us in building a secure future together.

The modern workforce is increasingly distributed, with employees working from various locations across the globe. This shift to remote and hybrid work models has amplified the need for effective and secure device management. Organizations must ensure that employees can access corporate resources seamlessly while maintaining stringent security protocols.
Remote Windows device management has emerged as a cornerstone of IT strategies, enabling businesses to oversee and secure devices outside traditional office environments. With Microsoft Intune, organizations gain robust tools for managing Windows devices remotely, ensuring productivity, compliance, and security for their distributed workforce.
Remote device management refers to the ability to oversee, monitor, and maintain devices from a central location, regardless of where they are physically located. It encompasses several services, including device provisioning, software deployment, compliance monitoring, and security enforcement.
For businesses relying on Windows devices, Windows remote device management ensures that devices operate efficiently and securely. This capability has become indispensable as remote work continues to grow.
Remote device management services are critical for ensuring operational continuity, especially in a distributed work environment. Without effective management, organizations face challenges such as inconsistent updates, security vulnerabilities, and reduced productivity.
Remote device management ensures that devices remain functional and up-to-date, regardless of their location. IT teams can deploy software updates, troubleshoot issues, and enforce policies without requiring physical access to devices. In a remote setting, devices are more vulnerable to cyberattacks. Remote management allows IT teams to implement Windows security control measures, ensuring that devices adhere to corporate security standards. Employees rely on their devices to perform their tasks efficiently. Remote management ensures that devices remain optimized, providing users with a seamless experience.
By leveraging Intune, organizations can implement Windows 11 remote device management strategies that align with modern workforce requirements. Intune supports device provisioning, policy enforcement, compliance monitoring, and security management, making it an essential tool for IT administrators.
Intune offers several features that address the challenges of managing Windows devices remotely. These capabilities ensure that businesses can maintain control over their device fleet while empowering employees to work from anywhere.
Intune simplifies the process of enrolling and provisioning Windows devices. IT teams can configure devices remotely, ensuring they are ready for use without requiring on-site setup. Automated provisioning saves time and reduces administrative overhead.
Through Intune, organizations can also enforce compliance policies tailored to their specific requirements. For example, devices can be configured to require encryption, enable firewalls, or restrict the installation of unauthorized software. Intune also monitors compliance in real-time, alerting administrators to potential violations. Additionally, Intune allows IT teams to manage applications on Windows devices remotely. This includes deploying corporate apps, updating software, and removing unauthorized applications. Application management ensures that employees have access to the tools they need while maintaining security.
Security remains one of the most vital aspects of remote device management, particularly as cyber threats grow in sophistication and frequency. In a distributed workforce, where employees access corporate data from diverse locations and networks, the risk of breaches, malware, and unauthorized access increases exponentially. Microsoft Intune rises to this challenge by integrating seamlessly with Windows security control mechanisms to provide comprehensive threat protection and ensure the safety of corporate data and infrastructure.
Malware continues to be a primary threat vector for businesses, especially with employees accessing resources from untrusted networks. Intune works in tandem with Microsoft Defender for Endpoint to provide advanced malware detection capabilities. This integration enables IT teams to identify, quarantine, and mitigate malicious files or software in real time. For example, if malware is detected on a managed device, Intune can initiate automated remediation steps, such as blocking the application, isolating the device from the network, and notifying IT administrators. This proactive approach minimizes potential damage and prevents the spread of threats across the organization.
Intune also offers real-time monitoring of devices, continuously assessing their security posture and identifying vulnerabilities. By leveraging Microsoft’s threat intelligence network, which analyzes billions of data points globally, Intune helps organizations stay ahead of emerging threats. Through a centralized dashboard, administrators gain visibility into the health and compliance status of all managed devices. Alerts for suspicious activities, such as unauthorized login attempts or unusual application behavior, are flagged immediately, allowing IT teams to respond swiftly and effectively.
Intune provides tools for remote support, allowing IT teams to troubleshoot and resolve issues without requiring physical access to devices. This capability is particularly valuable for distributed workforces, as it minimizes downtime and enhances productivity.
Intune containerization plays a crucial role in remote device management by separating corporate data from personal data on Windows devices. This approach ensures that sensitive corporate information remains secure, even on personal or shared devices.
Intune containerization creates distinct environments for corporate and personal data. The corporate container is governed by security policies, ensuring that sensitive information is encrypted, protected, and isolated. Personal data remains unaffected by corporate policies, preserving user privacy.
Containerization ensures that corporate data is isolated from the rest of the device, creating a secure environment governed by organizational policies. This separation protects sensitive information from unauthorized access or misuse, even if the device itself is compromised. By encrypting corporate data and applying strict access controls within the container, businesses can significantly reduce the risk of data breaches.
One of the key benefits of containerization is its ability to respect employees' personal privacy. By isolating corporate data from personal data, employees retain full control over their personal applications, files, and settings. This approach addresses common concerns about IT overreach, ensuring that personal content remains untouched by corporate policies or administrative actions.
Also, when an employee leaves the organization, containerization simplifies the process of securing corporate data. IT teams can remotely wipe the corporate container without affecting personal data on the device. This ensures that sensitive company information is removed while maintaining the integrity of the employee’s personal files and applications. This streamlined approach enhances security and provides a seamless offboarding experience for both the employee and the organization.
Remote work introduces unique security challenges that organizations must address to protect their data and infrastructure. Intune provides comprehensive tools to mitigate these risks and ensure secure operations.
Windows devices, like any other platform, are susceptible to security vulnerabilities. Intune enables IT teams to monitor and address these vulnerabilities proactively. For example, administrators can enforce regular updates, enable endpoint protection, and restrict access to high-risk applications. Intune supports zero-trust security principles, which assume that no user or device can be trusted by default. By requiring authentication and compliance verification for every access request, Intune minimizes the risk of unauthorized access. Intune ensures that corporate data is secure both in transit and at rest. Encryption protocols, secure VPN configurations, and data loss prevention policies protect sensitive information from interception or theft.
Beyond security, Intune plays a vital role in enhancing remote workers' productivity. By providing employees with the tools and resources they need, Intune ensures that work continues uninterrupted. Intune simplifies access to corporate resources by integrating with Microsoft’s broader ecosystem, including Azure Active Directory and Office 365. Employees can securely access files, applications, and collaboration tools from any location. Regular updates and proactive maintenance through Intune ensure that Windows devices remain optimized for performance. This reduces downtime caused by technical issues and enhances the overall user experience. Intune allows organizations to create customized workflows that align with their specific needs. For example, IT teams can configure devices to automatically connect to secure networks, synchronize with cloud storage, or install essential applications upon startup.
Managing a distributed workforce often involves additional costs, such as IT support, hardware procurement, and security measures. Intune helps organizations achieve cost efficiency by streamlining operations and reducing overhead. With Intune, organizations can support BYOD (Bring Your Own Device) policies, allowing employees to use their personal Windows devices for work. This reduces the need to purchase and maintain company-owned hardware. Remote support capabilities reduce the need for on-site IT visits, saving time and resources. Intune’s automation features further enhance efficiency, enabling IT teams to focus on strategic initiatives. Intune’s cloud-based infrastructure is inherently scalable, making it suitable for organizations of all sizes. As businesses grow, they can add new devices to their Intune environment without significant additional costs.
As remote work becomes a permanent fixture in the modern workplace, the importance of remote device management will continue to grow. Microsoft Intune is well-positioned to lead this transformation, with ongoing advancements in automation, artificial intelligence, and integration. Future developments may include enhanced predictive analytics for identifying potential device issues, tighter integration with emerging technologies, and even more granular security controls. These innovations will ensure that Intune remains a cornerstone of remote device management strategies.
Supporting a distributed workforce requires robust and secure device management solutions. Microsoft Intune provides a comprehensive platform for managing Windows devices remotely, addressing challenges such as security, compliance, and productivity. By leveraging features like containerization, compliance monitoring, and real-time support, Intune enables organizations to maintain control over their device fleet while empowering employees to work from anywhere. With its cost efficiency, scalability, and integration capabilities, Intune is an essential tool for businesses navigating the complexities of remote work.
As the workplace continues to evolve, remote device management remains a vital part of IT strategies. With Microsoft Intune services, organizations gain the tools and resources needed to manage devices securely and efficiently in an increasingly interconnected world. If your organization requires expert guidance on configuring Intune’s remote device management features and strengthening its security posture, contact CloudSolvers today.

Achieving compliance is not just a legal obligation but also a critical component of building trust with customers and stakeholders. For organizations relying on Windows devices, ensuring regulatory compliance can be a daunting challenge. Microsoft Intune offers a comprehensive solution to this challenge, providing the tools and features necessary to simplify compliance and maintain adherence to industry standards.
Regulatory compliance involves adhering to laws, regulations, and standards that dictate how organizations manage their data and devices. For businesses operating in industries such as healthcare, finance, and government, compliance requirements often include stringent measures for data protection, access control, and device security.
Windows devices, as integral tools in most business environments, must be managed in ways that align with these compliance requirements. Without proper oversight, these devices can become entry points for data breaches, unauthorized access, and other compliance violations. Microsoft Intune addresses these challenges by offering a centralized platform to enforce, monitor, and manage compliance policies across an organization’s device fleet.
At the heart of Microsoft Intune’s compliance capabilities are its compliance policies. These policies define the conditions devices must meet to be considered compliant with an organization’s standards. Intune compliance policies cover a wide range of parameters, including operating system versions, security settings, password requirements, and encryption standards.
For example, an organization can create a compliance policy that requires all Windows devices to have the latest security patches installed, use device encryption, and enforce a minimum password complexity. By implementing these policies, businesses ensure that their devices align with both internal security protocols and external regulatory standards. The Intune default device compliance policy acts as a baseline, applying a standard set of rules to all managed devices. This default policy ensures that unmanaged or non-compliant devices are flagged for review, preventing them from accessing corporate resources. Organizations can customize or expand upon this baseline to create more specific compliance policies tailored to their unique needs.
One of the primary advantages of Intune is its ability to simplify compliance management for Windows devices. The platform provides a range of tools and features that streamline the enforcement and monitoring of compliance policies. Intune compliance check capabilities automate the process of evaluating whether devices meet defined policies. Each device is regularly assessed against the set compliance criteria, and its status is updated in real-time. If a device falls out of compliance, Intune can take immediate action, such as restricting access to corporate resources or notifying administrators.
This automation eliminates the need for manual compliance checks, reducing the administrative burden on IT teams and ensuring that issues are identified and addressed promptly.
Device Health Attestation is a security feature in Microsoft Intune that verifies the health of Windows devices before granting them access to corporate resources. DHA checks critical security components such as Secure Boot, BitLocker encryption, and early-launch antimalware protection during the device startup process. If a device fails these checks, it can be flagged as non-compliant, triggering remediation actions like limiting access or enforcing additional security protocols. By leveraging Device Health Attestation, organizations can ensure that devices meet foundational security requirements, reducing the risk of malware infections and unauthorized access.
Intune’s centralized console provides a single point of control for managing compliance across an organization’s Windows devices. Administrators can create, modify, and deploy compliance policies from a unified interface, ensuring consistency and efficiency. This centralized approach is particularly beneficial for organizations with large or distributed workforces, as it simplifies the management of diverse device fleets.
Intune integrates seamlessly with Microsoft Entra ID’s Conditional Access capabilities, adding an extra layer of security to compliance management. Conditional Access policies allow businesses to enforce compliance requirements as a prerequisite for accessing corporate resources. For instance, a device that fails to meet compliance standards might be blocked from accessing sensitive applications or data until the issue is resolved. This integration ensures that non-compliant devices do not pose a risk to the organization while compliant devices enjoy seamless access to necessary resources.
To maximize the effectiveness of Intune compliance policies, organizations should follow best practices that align with their operational and regulatory needs. These practices not only enhance compliance but also improve overall security and efficiency.
The first step in creating effective compliance policies is to define clear and comprehensive requirements. Organizations should identify the specific standards they must adhere to, such as GDPR, HIPAA, or ISO 27001, and translate these requirements into actionable policies. For example, businesses handling sensitive customer data may require devices to use full-disk encryption, disable external storage, and enforce multi-factor authentication. These requirements should be clearly documented and regularly reviewed to ensure they remain relevant.
Not all devices within an organization have the same compliance needs. Intune allows administrators to create granular compliance policies for different device groups based on their roles, locations, or usage patterns. For instance, devices used by the finance department might require stricter security controls than those used in less sensitive roles. By tailoring policies to specific groups, organizations can strike a balance between security and usability.
Intune provides detailed reporting and analytics features that allow businesses to monitor compliance trends and identify potential risks. Administrators can generate reports on device compliance status, policy violations, and remediation actions, gaining valuable insights into their security posture. These reports can be used to demonstrate compliance during audits or to identify areas for improvement. By leveraging analytics, organizations can proactively address vulnerabilities and refine their compliance strategies.
The regulatory landscape is constantly evolving, and businesses must adapt to keep pace with new requirements. Intune enables organizations to update their compliance policies as needed, ensuring that they remain aligned with the latest standards.
For example, a new regulation might require businesses to implement stricter data encryption measures. Intune allows administrators to modify existing policies or create new ones to meet these requirements, ensuring continuous compliance.
Despite the best efforts to enforce compliance, there may be instances where devices fall out of compliance. Intune’s remediation capabilities play a crucial role in addressing these situations and minimizing their impact. By addressing non-compliance proactively, Intune minimizes the risk of regulatory violations and enhances overall security. When a non-compliant device is identified, Intune can take automated actions to mitigate the risk. These actions may include:
The rise of remote and hybrid work has introduced new challenges for compliance management. Employees accessing corporate resources from personal devices or unsecured networks can increase the risk of compliance violations.
Intune is uniquely equipped to address these challenges, providing tools to enforce compliance across remote and hybrid work environments. Features such as zero-touch deployment, Conditional Access, and remote management ensure that all devices remain compliant, regardless of location. For example, Intune can require remote devices to use secure VPN connections and adhere to encryption standards before accessing sensitive data. These measures protect the organization while enabling employees to work productively from anywhere.
Compliance is not a one-time achievement but an ongoing process that requires regular evaluation and improvement. Intune supports this iterative approach by providing insights and tools that help organizations refine their compliance strategies over time. Administrators can use Intune’s analytics and reporting features to assess the effectiveness of their compliance policies and identify areas for improvement. For instance, a report might reveal that a particular policy is frequently violated due to user error or technical limitations. This insight can inform changes to the policy or the implementation of additional training programs.
By fostering a culture of continuous improvement, organizations can maintain compliance more effectively and adapt to evolving regulatory requirements. Regulatory adherence not only mitigates legal and financial risks but also builds trust with customers and stakeholders. Microsoft Intune offers a comprehensive solution for managing compliance and simplifying the enforcement and monitoring of policies across an organization’s device fleet.
From creating customized compliance policies to automating compliance checks and addressing non-compliance, Intune provides the tools necessary to navigate the complex regulatory landscape. Its integration with Conditional Access and robust reporting features further enhance its capabilities, making it an essential platform for meeting regulatory standards. By adopting Intune compliance policies and following best practices, businesses can ensure that their Windows devices remain secure, efficient, and compliant. Whether supporting remote work, managing large device fleets, or preparing for audits, Intune empowers organizations to achieve compliance with confidence and ease. Get in touch with CloudSolvers’ Intune experts today to discover how we can assist you in implementing and optimizing Microsoft Intune. Together, we’ll build a secure, compliant, and future-ready IT environment for your organization.

Efficient hardware management is a cornerstone of sustainable business operations in the modern era. The lifecycle of devices, from procurement to retirement, directly impacts organizational costs, productivity, and overall efficiency. With mobile device lifecycle management (MDLM), businesses can streamline how they handle hardware assets, reduce expenses, and optimize resources. Microsoft Intune, a robust Mobile Device Management (MDM) platform, is a powerful tool for managing the lifecycle of Windows devices effectively. By leveraging Intune's MDM lifecycle management features, businesses can maximize device value while minimizing associated costs.
Mobile Device Lifecycle Management refers to the strategic process of managing devices through their entire lifecycle, encompassing acquisition, configuration, use, maintenance, and eventual retirement. Proper MDLM ensures that businesses derive maximum value from their hardware investments while mitigating the risks of obsolescence, inefficiency, and security vulnerabilities.
The increasing reliance on mobile and portable devices in workplaces has expanded the scope of device lifecycle management. With employees using laptops, tablets, and other mobile devices for remote and hybrid work, organizations must adopt solutions that provide visibility and control over these assets. Intune’s MDM lifecycle management capabilities offer a comprehensive framework to manage the lifecycle of Windows devices with precision and efficiency.
The first stage of the mobile device lifecycle involves procurement and deployment. Businesses must carefully select devices that align with their operational needs, balancing performance, durability, and cost. However, the challenge often lies in configuring and deploying these devices efficiently, especially when dealing with a large workforce.
Microsoft Intune simplifies this process by automating device provisioning and configuration. With zero-touch deployment capabilities, new devices can be set up remotely, reducing the need for IT staff to physically handle each unit. This saves significant labor costs and accelerates the onboarding process.
Intune also supports Windows Autopilot, a feature that streamlines the initial setup of Windows devices. Autopilot allows businesses to customize device configurations based on user roles, ensuring that each device is optimized for productivity from the start. This seamless deployment process minimizes downtime and reduces the costs associated with manual configuration errors.
Once devices are deployed, the focus shifts to optimizing their usage and performance. Efficient device management during this stage can significantly extend the lifespan of hardware, reducing the frequency of replacements and associated costs. Intune provides administrators with tools to monitor device performance and enforce policies that enhance security and functionality. For example, administrators can use Intune to push regular updates, ensure compliance with security standards, and manage applications remotely. These features ensure that devices remain up-to-date, secure, and free from performance issues that could lead to premature obsolescence.
Mobile device lifecycle management also involves monitoring device utilization. Intune offers detailed insights into how devices are being used, allowing businesses to identify underutilized or redundant hardware. By reallocating or decommissioning these devices, organizations can avoid unnecessary procurement costs and make better use of their existing assets.
Hardware failures and performance issues are inevitable, but their impact on productivity and costs can be mitigated through proactive maintenance and efficient troubleshooting. Intune’s MDM lifecycle management features enable businesses to address these challenges effectively. With remote management capabilities, Intune allows IT administrators to diagnose and resolve issues without requiring physical access to the device. This not only saves time but also eliminates the need for costly on-site visits. Features like remote reset, configuration updates, and troubleshooting tools ensure that issues are resolved promptly, minimizing downtime and its associated costs.
Proactive maintenance is another critical aspect of the device lifecycle. Intune enables businesses to schedule regular updates, monitor hardware health, and identify potential issues before they escalate. For example, administrators can track battery performance or storage usage, allowing them to address problems proactively and extend the lifespan of devices.
Security is a fundamental concern at every stage of the mobile device lifecycle. A breach or compromise can lead to significant financial and reputational losses. Intune plays a pivotal role in securing Windows devices throughout their lifecycle, ensuring that businesses remain protected without incurring additional costs for third-party solutions.
Intune facilitates the management and integration of robust security features such as device encryption, Local Administrator Password Solution (LAPS), multi-factor authentication, and Conditional Access policies. These measures collectively protect sensitive data, prevent unauthorized access, and mitigate the risk of costly security breaches. By seamlessly integrating with Microsoft Defender for Endpoint, Intune empowers organizations with advanced threat detection and response capabilities, further bolstering device security. During the device retirement phase, security remains a critical consideration. Intune ensures that sensitive data is removed from devices before they are decommissioned or repurposed. Remote wipe capabilities allow administrators to erase corporate data without affecting personal files, making it easier to securely transition devices to their next stage of use.
Replacing devices prematurely can significantly increase hardware costs. By extending the lifespan of Windows devices, businesses can reduce capital expenditures and allocate resources more effectively. Intune’s lifecycle management features are designed to maximize device longevity while maintaining optimal performance and security.
One way Intune achieves this is through predictive analytics and performance monitoring. Administrators can use these insights to identify devices nearing the end of their usable lifespan or requiring upgrades. By addressing issues like outdated hardware or software inefficiencies early, businesses can avoid disruptions and extend device usability. Intune also supports phased rollouts of updates and configurations, ensuring that changes are implemented smoothly and without overwhelming older hardware. This gradual approach minimizes the risk of compatibility issues and allows businesses to make the most of their existing investments.
The final stage of the mobile device lifecycle is retirement, where devices are either decommissioned, repurposed, or recycled. Proper management during this phase is essential to minimize costs and environmental impact. Intune simplifies the retirement process by providing tools to securely wipe devices and prepare them for resale or donation. Businesses can also use Intune to manage device recycling programs, ensuring compliance with environmental regulations and corporate sustainability goals.
For organizations adopting a circular economy approach, Intune facilitates the transition of devices to secondary users within the company. For example, older devices can be repurposed for non-critical tasks or assigned to temporary employees, reducing the need for new hardware purchases.
As businesses grow, so does the complexity of managing an expanding fleet of devices. Intune’s scalability ensures that organizations can maintain control over their hardware assets without incurring excessive administrative costs. Intune’s centralized dashboard provides a single point of control for managing all Windows devices, regardless of their location or usage. This unified approach simplifies inventory management, policy enforcement, and compliance tracking, allowing businesses to scale their operations efficiently.
For multinational organizations, Intune offers multi-language and multi-region support, ensuring consistent device management across global teams. This eliminates the need for separate solutions in different regions, reducing costs and administrative overhead.
The rise of hybrid and remote work has added new dimensions to the challenges of device lifecycle management. Employees working from home or other remote locations require secure and reliable access to corporate resources, increasing the demand for effective MDM solutions. Intune is uniquely equipped to address these challenges, providing businesses with the tools needed to support remote work without compromising security or efficiency. Features like zero-touch deployment, remote management, and Conditional Access ensure that remote devices remain secure and compliant throughout their lifecycle.
By enabling remote troubleshooting and maintenance, Intune reduces the costs associated with supporting distributed teams. Employees can remain productive while IT teams manage devices seamlessly, regardless of physical location.
Device lifecycle management is not a static process; it requires ongoing evaluation and improvement to keep pace with evolving business needs and technological advancements. Intune provides businesses with the insights and tools needed to refine their MDLM strategies continuously.
Through detailed reporting and analytics, Intune allows organizations to assess the performance and usage of their devices over time. These insights can inform decisions about procurement, configuration, and maintenance, ensuring that businesses maximize the value of their hardware investments.
By staying proactive and adaptive, businesses can leverage Intune to create a dynamic MDLM strategy that reduces costs, enhances efficiency, and supports long-term growth.
Windows device lifecycle management is an essential aspect of modern business operations, directly impacting costs, productivity, and security. By adopting a comprehensive MDLM approach with Microsoft Intune, organizations can streamline their processes, reduce hardware expenses, and maximize the value of their devices. From procurement and deployment to maintenance and retirement, Intune provides businesses with the tools they need to manage every stage of the device lifecycle effectively. Its robust features, including zero-touch deployment, predictive analytics, and remote management, ensure that devices remain secure, efficient, and cost-effective throughout their lifecycle.
As businesses navigate the challenges of hybrid work, expanding device fleets, and evolving security threats, Intune services offer robust MDM lifecycle management capabilities that drive success. By reducing hardware costs and optimizing device usage, organizations can focus on their core goals while maximizing technology investments. Reach out to CloudSolvers today to learn how our Intune services can help you deploy and optimize Microsoft Intune for a more cost-effective and sustainable device ecosystem. Together, we’ll build a secure and resilient future for your organization.

Today’s workplace is characterized by a highly mobile workforce, with employees relying on laptops, tablets, and other mobile devices to stay productive from anywhere. This shift towards mobility, while increasing flexibility and productivity, also introduces significant security challenges.
As businesses adopt this mobile-first approach, managing and securing Windows devices has become a top priority. Mobile Device Management (MDM) solutions, particularly Microsoft Intune, are pivotal in addressing these challenges by providing robust security, centralized management, and compliance enforcement for all Windows endpoints.
Mobile Device Management (MDM) for Windows is no longer optional for businesses. With employees accessing corporate data from various devices and locations, the attack surface for cyber threats has expanded dramatically. Mobile devices are often targeted by cybercriminals because of their ubiquity and the sensitive information they hold.
MDM solutions, like Microsoft Intune, allow organizations to maintain control over these devices while ensuring they meet stringent security requirements. By managing and monitoring mobile devices, businesses can safeguard their networks, protect sensitive data, and reduce the risk of data breaches or ransomware attacks.
Microsoft Intune stands out as a leading MDM solution for Windows devices, offering a cloud-based platform that integrates seamlessly with the Microsoft ecosystem. As part of Microsoft Endpoint Manager, Intune provides businesses with a centralized console to manage and secure their devices, applications, and data.
Intune's mobile device management capabilities for Windows ensure that businesses can deploy security policies, enforce compliance, and monitor device activity across their workforce. By leveraging Intune security features, organizations can reduce vulnerabilities and ensure that devices remain protected against ever-evolving cyber threats.
The growing reliance on mobile devices has introduced unique security challenges. Unlike traditional desktop systems, mobile devices are frequently used in unsecured environments, such as public Wi-Fi networks or shared workspaces. This increases their susceptibility to attacks like phishing, malware, and unauthorized access.
Microsoft Intune addresses these challenges by implementing mobile device management security features tailored for Windows devices. These include real-time monitoring, remote access control, and encryption enforcement. Intune also supports multi-factor authentication (MFA) and Conditional Access policies, ensuring that only verified users can access corporate resources.
One of Intune's key strengths is its ability to enforce security baselines across all devices. Managing a large fleet of Windows devices can be a daunting task, particularly when onboarding new employees or replacing old hardware. Microsoft Intune simplifies this process by automating device provisioning and configuration. When a new device is enrolled in Intune, it automatically receives the necessary security policies, applications, and settings based on the user's role and the organization's requirements.
This ensures that every Windows device complies with organizational policies, regardless of whether it's used in the office or remotely. For example, Intune can mandate that devices have secure boot enabled, antivirus software active, and the latest security patches installed before granting access to corporate networks. This streamlined onboarding process not only saves time but also ensures that devices are secure from the moment they are activated. Administrators can use Intune to remotely deploy updates, revoke access, or reset devices as needed, providing a high level of control and flexibility.
In an era where data breaches can have catastrophic consequences, protecting sensitive information is paramount. Mobile Device Management security features in Intune ensure that data remains protected on Windows devices, even in the event of theft, loss, or unauthorized access. Intune supports robust data protection measures, including encryption, remote wipe capabilities, and app-specific policies. For instance, administrators can configure Intune to wipe corporate data from a device without affecting personal files, a feature that is particularly useful in bring-your-own-device (BYOD) environments.
Compliance is another critical aspect of MDM. Businesses must adhere to various regulatory requirements, such as GDPR, HIPAA, or ISO 27001, depending on their industry. Intune's compliance features allow organizations to enforce and monitor adherence to these regulations. Administrators can define compliance policies, generate reports, and take automated actions when devices fall out of compliance, ensuring that the organization remains audit-ready.
Visibility is a cornerstone of effective security. Without clear insights into device activity, administrators are left in the dark, unable to identify vulnerabilities or respond to threats effectively. Microsoft Intune bridges this gap by providing businesses with granular visibility into their Windows devices. This capability enables IT teams to monitor usage patterns, detect anomalies, and respond to potential threats in real time.
Intune’s seamless integration with Microsoft Defender for Endpoint elevates endpoint security by adding advanced threat detection, analytics, and automation. For instance, if unusual activity, such as unauthorized file access, privilege escalation attempts, or efforts to bypass security protocols, is detected, Intune can automatically trigger alerts, log the activity for analysis, and even initiate predefined remediation actions.
This proactive approach extends beyond detection to facilitate continuous compliance monitoring. Administrators can leverage Intune to enforce security baselines, ensure devices meet organizational policies, and dynamically adjust configurations in response to evolving threats. These measures ensure that endpoints remain protected while minimizing disruptions to productivity.
Moreover, Intune’s centralized dashboard offers a unified view of endpoint health and security across the enterprise, simplifying management and accelerating incident response. By integrating threat intelligence, real-time insights, and automated workflows, Intune empowers organizations to stay ahead of cyber threats, addressing vulnerabilities before they are exploited and fostering a more resilient security posture.
The rise of remote and hybrid work has fundamentally changed how businesses operate, making mobile device management for Windows more important than ever. Employees frequently use personal or unmanaged devices to access corporate resources, introducing significant security risks.
Microsoft Intune provides businesses with the tools needed to secure and manage these remote endpoints effectively. Through features like Conditional Access, Intune ensures that only compliant devices can access sensitive data, regardless of location. Administrators can also enforce network security protocols, such as VPN usage or Wi-Fi restrictions, to protect remote connections.
For organizations with hybrid work models, Intune offers a unified platform to manage both on-premises and remote devices. This eliminates the need for multiple tools and reduces the complexity of managing diverse work environments.
Mobile device management extends beyond securing hardware; it also involves managing the applications employees use to perform their work. Intune offers robust application management features that ensure only approved apps are installed and used on Windows devices.
Administrators can deploy, update, and remove applications remotely, reducing the risk of employees installing unauthorized or malicious software. Intune also supports app-specific security policies, such as restricting copy-and-paste functions or preventing data sharing between corporate and personal apps.
Additionally, Intune integrates with Microsoft Azure Active Directory to provide secure access to cloud applications. By leveraging single sign-on (SSO) and Conditional Access, businesses can streamline user authentication while maintaining a high level of security.
As cyber threats continue to evolve, businesses must adopt forward-thinking strategies to stay protected. Mobile Device Management for Windows, powered by Microsoft Intune, ensures that organizations are prepared for the challenges of tomorrow.
Microsoft Intune’s continuous updates and seamless integration with Microsoft’s security ecosystem equip businesses with advanced tools to combat emerging cyber threats. When paired with Microsoft Defender for Endpoint, organizations gain access to features like machine learning-powered threat detection, automated incident response, and zero-trust security enforcement. This comprehensive approach positions Intune as a future-ready solution for managing and securing Windows devices.
Mobile Device Management for Windows is no longer a luxury but a necessity for modern businesses. With employees relying on mobile devices to access corporate data from anywhere, organizations must prioritize security and management to protect their digital assets.
Microsoft Intune stands out as a comprehensive MDM solution, offering advanced security features, centralized management, and seamless integration with the Microsoft ecosystem. From enforcing compliance and protecting sensitive data to supporting remote work and future-proofing security, Intune provides everything businesses need to thrive in a mobile-first world.
By adopting Windows Intune Mobile Device Management, businesses can secure their workforce, boost productivity, and gain peace of mind knowing their devices and data are protected against an ever-evolving threat landscape. Contact CloudSolvers’ Microsoft Intune consultants today for expert advice on safeguarding all devices across your organization.

