As of 2024, 57% of organizations report experiencing phishing attempts weekly or even daily. With phishing accounting for 80% of IT security incidents, it’s estimated that businesses lose approximately $17,700 every minute due to phishing-related issues.
This makes phishing one of the largest threats to your organization. Thankfully, Microsoft Intune has you covered and can offer peace of mind to leaders focused on data protection.
Microsoft Intune integrates with Defender for Enpoints and enables administrators to manage conditional access policies to help mitigate phishing attempts and the damage they can do to your organization.
Conditional Access, part of Microsoft Entra ID (formerly Azure Active Directory), enables organizations to create policies that combine user, device, and application signals to determine access permissions.
Intune integrates with Conditional Access to enhance security by enforcing device compliance and app protection policies. This ensures a secure, flexible experience for users to access corporate resources from various devices and locations.
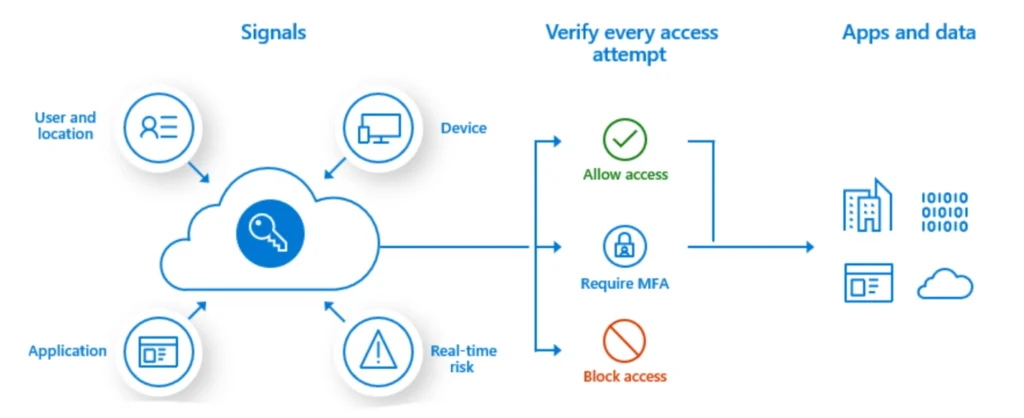
The first line of defense is device-based conditional access. Intune and Entra ID ensure that only devices managed through Intune can access organizational resources like email, SaaS applications, and other important applications and information.
You can also make it so that only domain-joined devices enrolled in Intune can have access to Microsoft 365 services based on network access, device risk, or whether or not they are on-premises.
Microsoft Intune enforces policies using various signals to ensure security and compliance. It can restrict access based on organizational roles, enforce standards like operating system versions and security configurations, ensure that only managed applications access sensitive data, adjust restrictions based on location, and leverage real-time risk assessments through integration with Microsoft Defender.
Keep in mind that the complaint network location features are only supported by devices enrolled in mobile device management (MDM). Users who aren’t enrolled in MDM may be blocked from accessing key resources.
Microsoft Defender SmartScreen’s Enhanced Phishing Protection is an advanced security feature that safeguards users from phishing attacks by providing proactive warnings and mitigation strategies. This feature integrates seamlessly into the operating system, offering an extra layer of defense for sensitive information like passwords, preventing their exposure to unsafe applications, websites, and processes.
Features such as these integrate with Microsoft Intune allowing IT administrators to configure and enforce policies related to phishing protection.
This integration provides organizations with a centralized mechanism to protect user credentials across all managed devices, ensuring compliance with security standards. Administrators can enable or customize phishing protection features, such as warning users against password reuse or preventing unsafe password storage and blocking malicious websites, to align with organizational security policies.
Enhanced Phishing Protection works dynamically, leveraging Microsoft’s intelligent threat detection systems to identify potential risks when users enter passwords into websites or applications.
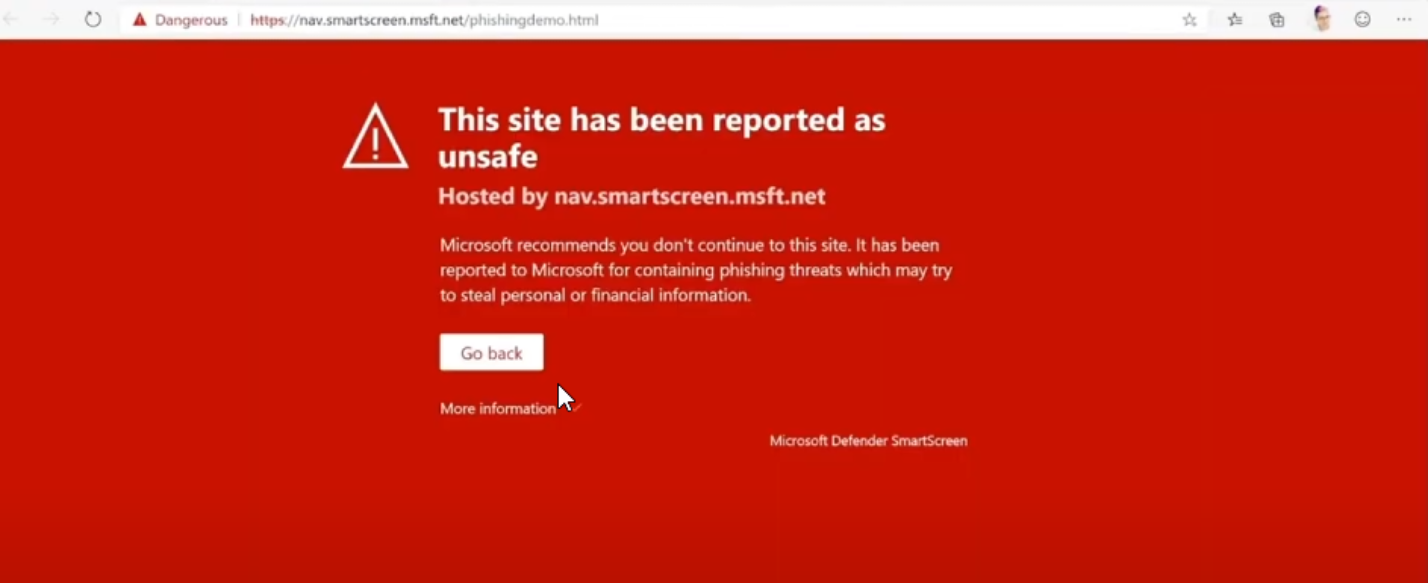
For instance, if a user enters their Microsoft account password into a known malicious or unfamiliar website, SmartScreen triggers a warning.
This alert is a result of extensive analysis, which includes evaluating the site’s reputation and the context of the password entry. The warning prompts users to reconsider their actions, offering advice on best practices for safeguarding credentials.
This feature is also designed to prevent the reuse of corporate passwords across personal applications or sites. Password reuse is critical because it increases the risk of credential stuffing attacks, where cybercriminals exploit reused passwords across multiple sites to gain unauthorized access.
By discouraging and alerting users to this behavior, Enhanced Phishing Protection helps mitigate such vulnerabilities and reinforces better password hygiene.
Another significant aspect of Enhanced Phishing Protection is its ability to detect unsafe storage of passwords. Users sometimes store passwords in plain text files or unencrypted documents on their devices, which malicious actors can easily access.
SmartScreen scans these files and alerts users when such unsafe storage practices are detected, encouraging them to adopt more secure methods of storing credentials.
SmartScreen’s capabilities are further enhanced through its connection with the broader Microsoft security ecosystem. It leverages threat intelligence from Microsoft Defender, enabling it to stay updated with the latest phishing trends and malicious domains.
This real-time intelligence helps ensure that SmartScreen can quickly identify and block emerging threats, providing users with up-to-date protection and supporting a user-centric approach to security by offering clear and actionable guidance when alerts are triggered. Instead of overwhelming users with technical jargon, SmartScreen presents straightforward instructions on how to mitigate the detected threat.
For example, if a user is warned about password reuse, the system provides recommendations for creating strong, unique passwords or using a trusted password manager.
In enterprise environments, Enhanced Phishing Protection offers additional benefits by integrating with security monitoring and reporting tools. IT teams can view insights into phishing attempts and user behavior, enabling them to identify trends and potential vulnerabilities. These insights support proactive security measures, helping organizations stay ahead of evolving threats.
Attack Surface Reduction (ASR) rules, an integral feature of Microsoft Defender with Intune, are critical in safeguarding organizational networks against various cybersecurity threats. Designed to minimize the exploitable vulnerabilities in an enterprise’s IT infrastructure, ASR rules target the techniques commonly used by malicious actors. These techniques often exploit gaps in application behavior, scripting engines, and user activities to gain unauthorized access or deploy harmful payloads.
By enforcing strict control over specific types of activities, ASR rules reduce the risk of breaches, enhancing the organization’s overall security posture.
ASR rules are proactive security measures that prevent threats before they execute. Rather than relying solely on post-execution detection mechanisms, these rules block potentially harmful actions at the source. This approach is vital for combating advanced persistent threats (APTs) and zero-day exploits, where traditional antivirus solutions may lag in detection. For example, ASR rules can prevent untrusted applications from launching child processes, blocking a common tactic used in lateral movement within networks or in malware propagation.
The implementation of ASR rules provides organizations with a granular level of control over device activities. Administrators can configure rules to suit their unique security requirements, striking a balance between stringent protection and operational flexibility.
Each rule targets specific behaviors, such as executing scripts from email attachments, embedding macros in Office files, or attempting code injection. These rules are often based on the analysis of attack patterns observed in the wild, ensuring that they address real-world threats.
Integration with Microsoft Defender allows ASR rules to leverage insights from the broader Microsoft security ecosystem. This integration ensures that rules are continuously updated to reflect the latest threat intelligence, enabling real-time defense against evolving cyberattacks.
The system also provides detailed reporting and alerting features, giving administrators visibility into rule enforcement and blocked activities. This data can be used to refine security policies, ensuring they remain effective without causing unnecessary disruptions.
A key feature of ASR rules is their ability to operate in audit mode. This mode allows administrators to test the impact of specific rules before fully enforcing them. By logging the activities that would have been blocked, organizations can evaluate the potential operational impact and adjust rules accordingly. This approach minimizes the risk of false positives, ensuring that legitimate business processes are not hindered by overly restrictive policies.
ASR rules address the human element of cybersecurity, recognizing that user actions are a significant vector for threats. By blocking actions like running executable content from email attachments and other phishing attempts, ASR rules help mitigate risks associated with user errors or deliberate misuse. These measures are particularly important in mitigating phishing attacks, which often rely on tricking users into executing malicious files or links.
In addition to targeting application behaviors, ASR rules can be configured to protect against credential theft. For instance, rules can prevent processes from accessing local security authority subsystem service (LSASS) memory, a technique often used in credential dumping attacks. This capability is critical in environments where sensitive credentials, such as administrator passwords, are prime targets for attackers.
ASR rules are not a standalone solution but a critical component of a layered security strategy. They complement other Microsoft Defender features, such as endpoint detection and response (EDR), vulnerability management, and network protection. Together, these tools create a comprehensive defense-in-depth approach capable of addressing threats across all stages of the attack lifecycle.
For organizations operating in highly regulated industries, ASR rules also offer compliance benefits. By demonstrating proactive measures to secure endpoints and reduce attack surfaces, businesses can meet regulatory requirements and improve their security audits. This added layer of accountability reinforces trust with stakeholders and aligns security efforts with broader organizational goals.
Microsoft’s Attack Simulation Training offers organizations an effective way to assess and enhance their security preparedness against phishing attacks. The tool enables administrators to create and run realistic simulations of common social engineering techniques, such as credential harvesting, malware attachments, and drive-by URLs. By testing user susceptibility to these simulated threats, organizations can identify vulnerabilities and address them before they are exploited in real-world scenarios.
Setting up a simulation involves using the Microsoft Defender portal to configure attack parameters, including the type of threat, payload delivery method, and target recipients. Administrators can schedule simulations and monitor their progress in real-time. Once a campaign is complete, the tool provides detailed analytics, showing how users interacted with the simulated phishing emails. You can then use these insights to highlight areas for improvement and guide the development of tailored security awareness training.
Integration of attack simulation training into the broader Microsoft security ecosystem ensures a seamless and comprehensive approach to organizational defense. By combining technical safeguards with user education, you can foster a security-first culture, strengthen an organization’s ability to mitigate risks, stay ahead of evolving threats, and maintain a resilient cybersecurity posture.
The ability to customize Intune’s various tool rules is one of its strengths, but it also underscores the importance of continuous monitoring and refinement. Cyber threats are dynamic, and security measures must adapt to remain effective.
Administrators should regularly review rule and policy performance, analyze blocked activities, and update configurations based on the latest threat intelligence. This iterative process ensures your policies remain relevant and effective against emerging threats. Although not an Intune feature, the Microsoft Defender simulation training platform is an innovative solution designed to bolster an organization’s cybersecurity defenses, providing a centralized hub for simulating phishing and other cyberattack scenarios. This tool enables businesses to simulate real-world cyberattacks, train employees to recognize and mitigate threats, and ultimately improve overall security posture.
The platform equips companies with the knowledge and tools necessary to stay ahead of potential threats. Unlike traditional methods, which often rely on static modules, this platform offers dynamic and engaging training sessions that are automatically customized based on an employee’s performance in simulated attacks. For instance, if an employee falls for a simulated phishing email, the platform assigns targeted training to address that specific vulnerability. This adaptive learning process ensures that employees are continuously improving their awareness and response capabilities.
Phishing attacks remain one of the most significant cybersecurity threats organizations face, causing widespread damage and financial loss. With Microsoft Intune’s robust integration with tools like Defender SmartScreen, Conditional Access, and Attack Surface Reduction rules, your organization can stay ahead of phishing attempts and other cyber threats. Intune empowers administrators to enforce tailored security policies, safeguard sensitive data, and create a secure environment for users—no matter where they work.
Ready to fortify your organization’s defenses against phishing attacks? Contact CloudSolvers today to learn how our expert Intune services can help you implement and optimize Microsoft Intune for comprehensive protection. Let’s work together to secure your future.